Mainly being driven from the rapidly evolving technology landscape .
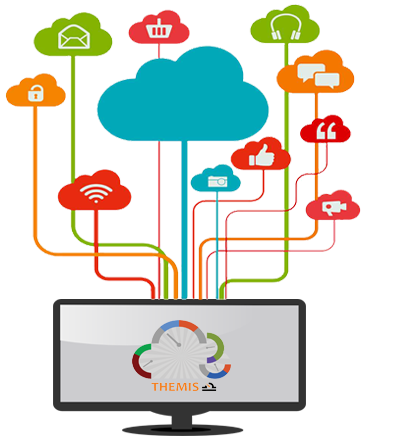
Step1: User attempts a login an application, an authentication request is sent to Themis service.
The login service be set-up to use existing business identity or allows user to bring their own social identities.

Step2: The Themis service gathers contextual and behavioural data on the identity of the user and runs it through the risk engine.
Step3: The Risk engine produces a risk score which is sent back to the authentication service.
The engine learns about the user as they use the service so ease of use improves.
Step4: The authentication service then acts on the risk score using the business policy configured for that application. Either the user is allowed access, Stepped up (2nd factor) or denied access. Simple right!
Step3: The Risk engine produces a risk score which is sent back to the authentication service.